If your board asked, “Who holds the keys, where do control planes run, and how fast can we produce audit evidence?”—could you answer in 30 seconds? That’s the sovereignty test enterprises, MSPs, and public bodies are facing right now. With the EU’s AI Act moving ahead, DORA now live for financial entities, and NIS2 tightening cybersecurity expectations across critical sectors, “data residency” alone is no longer a credible story—it’s about operational sovereignty you can prove on demand.
To move beyond ‘data residency’ as a credible story, a new model is required—one that you can test, score, and prove on demand. We’ve distilled this complex challenge into a go-to framework covering the Four Layers of Sovereignty and Three Practical Deployment Modes. This post introduces this model and shows how to operationalize it, turning compliance from a cost center into a velocity engine for your engineering teams.
Two forces converged in 2024–2025. Regulation hardened: the EU AI Act advanced with new transparency duties; DORA became binding on 17 Jan 2025, elevating oversight of critical ICT third parties; NIS2 extended control-and-proof expectations across essential/important entities. In practice, this means customer-held keys (CMK/HSM), in-region control planes, no-egress by default, metadata residency, and audit-ready artifacts showing who changed what, when, and under which control.
Meanwhile, the market realigned: hyperscalers introduced EU-governed constructs—e.g., AWS’s €7.8B European Sovereign Cloud (first region planned in Brandenburg by end-2025) and Microsoft’s expanded EU Data Boundary (now covering system-generated logs and pseudonymized personal data). And at the model layer, Europe shipped openness and scrutiny with Apertus, a fully open, multilingual LLM—great for trust and auditability, but still dependent on sovereignty controls where the model runs.
Over the past year, a collision of regulatory hardening (DORA, NIS2), the rise of sovereign cloud regions, and intense board-level scrutiny has created a new reality: residency is no longer enough.
The C-suite isn’t asking for assurances; they are demanding provable sovereignty. This isn’t a single conversation; it’s four different ones, each with its own language of risk and value. To be effective, you must translate the abstract goal of “sovereignty” into the specific proofs each leader needs to see.
The Chief Financial Officer needs to see sovereignty as a predictable financial model, not just a compliance cost. They expect a defendable unit-economics breakdown (€/vCPU, €/GiB) backed by hard evidence of enforced savings levers, like automated rightsizing policies and egress allow-lists.
Red flags: “Visibility-only” dashboards and savings claims that cannot be independently verified.
For the Chief Information Security Officer, sovereignty is a set of non-negotiable technical controls. They require customer-managed keys (CMK/HSM), strictly in-region control planes, and a no-egress-by-default network policy. This posture must be enforced with policy-as-code and proven with immutable artifacts that detail exactly who did what, when, and under which authority.
Red flags: Provider-scanned content, global control paths, and any operational log leaving the jurisdiction.
The Data Protection Officer views sovereignty through the lens of compliance and proof. They need DPIA-ready evidence on demand—verifiable retention policies, access attestations, and key-custody records. These must be exportable, time-stamped audit packs aligned to NIS2 and GDPR, not static screenshots from a console.
Red flags: Manual evidence collection, undocumented exceptions, and mixed-jurisdiction staff performing privileged operations.
The Chief Technology Officer is tasked with making sovereignty an accelerator, not a bottleneck. They must provide developers with “paved roads” in CI/CD that embed automated controls and safe exception workflows. To maintain leverage, they need guarantees of in-region control planes and the ability to port not just workloads, but all their associated audit artifacts.
Red flags: Ticket-driven security gates, any drift between declared policy and runtime reality, and bespoke configurations that kill scalability.
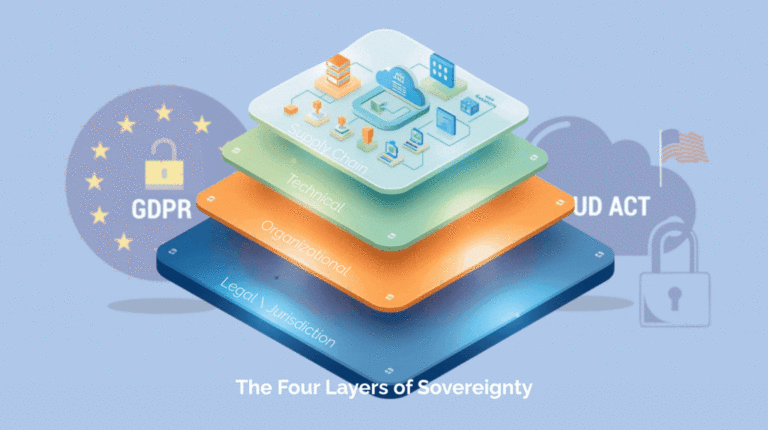
To separate signal from noise, you need a pragmatic model that moves beyond simple checklists. Our framework provides a holistic structure, recognizing that true sovereignty is a stack of interdependent controls where a failure in one layer can undermine the entire effort.
It begins with the foundational Legal and Organizational Layers, which establish the contractual and human firewall—defining your jurisdiction, audit rights, and who is permitted to perform privileged operations. But policy is not proof. The Technical Layer is where you enforce these rules in software, using customer-held keys, in-region control planes, and policy-as-code to generate immutable evidence. Finally, the Supply Chain Layer ensures your sovereignty isn’t compromised by a third-party vendor, requiring attestations and clear sourcing strategies.
With this layered model, you can then choose a practical deployment strategy. You might aim for a Fully Sovereign mode in your own facilities or leverage a Sovereign-Operated Public Cloud. Crucially, there is a Transitional mode—a pragmatic starting point that allows you to lock down the hard technical controls immediately while you mature your organizational and supply chain processes.
The key is to move from guessing to measuring. In practice, this means scoring your capabilities across each layer and building a phased roadmap based on your risk appetite. The full whitepaper provides the complete scorecard, real-world examples, and buyer checklists to put this framework into action.
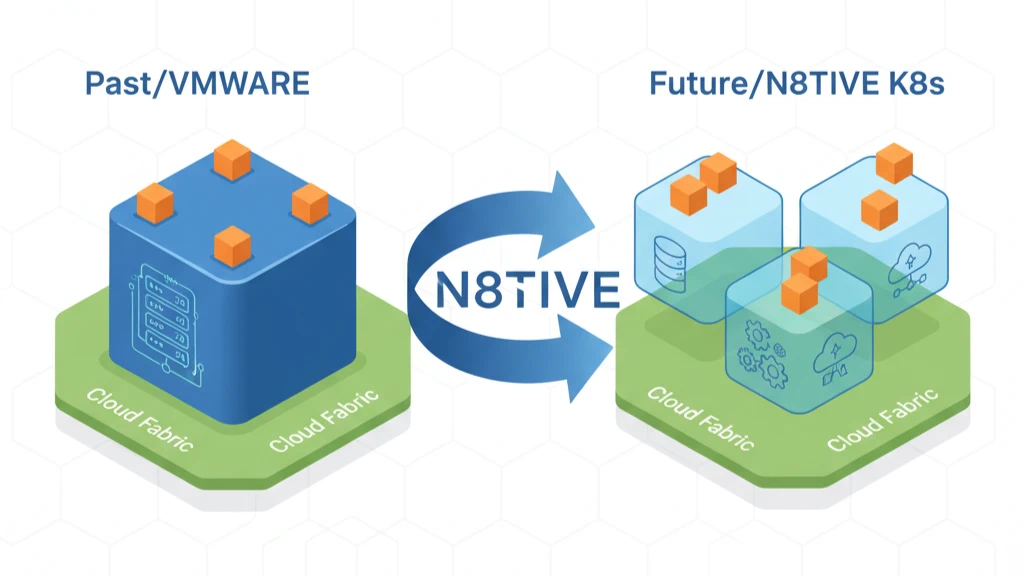
Frameworks define a strategy; a platform is what gives you the tools to execute it. N8TIVE is not sovereignty itself; it is the all-in-one platform layer that empowers you to achieve it. Running on any infrastructure—from hyperscalers like AWS or Azure to your own private cloud—N8TIVE provides the unified controls and automated evidence you need to build the precise sovereignty posture your business demands.
N8TIVE is engineered to provide the capabilities to master every aspect of the Four-Layer Sovereignty model:
To Enforce Your Organizational & Legal Policies (Layers 1 & 2): Your policies, our enforcement tools. N8TIVE provides the features you need to translate legal requirements into reality, including granular Role-Based Access Control (RBAC) and centralized customizable compliance reporting. As a European-owned entity, we provide these tools as a trusted partner, ensuring your core operational layer is aligned with your jurisdictional goals.
To Actively Enforce Technical Controls (Layer 3): We provide the universal control plane to enforce your technical rules consistently across any cloud. N8TIVE gives your teams the built-in tools for secret management, IaC-driven networking, and certificate control, allowing you to implement customer-held keys, in-region control planes, and no-egress policies, regardless of the infrastructure underneath.
To Achieve Strategic Control of Your Supply Chain (Layer 4): N8TIVE’s architecture gives you ultimate leverage. By abstracting the infrastructure layer, we turn the underlying cloud provider into a commodity. This delivers true portability, allowing you to move both workloads and their complete audit artifacts between vendors without operational disruption. This abstraction is your most powerful tool for mitigating vendor lock-in and maintaining strategic control.
Your Playbook for Provable Sovereignty
This framework is designed for action. Here is how leaders across different roles can use it to drive meaningful change, turning compliance from a roadblock into a strategic asset.
In a market disrupted by vendor licensing changes, your opportunity is to elevate your business model. Instead of merely reselling commodity cloud services, use this moment to productize a premium ‘Sovereignty-as-a-Service’ offering. Build a multi-tenant platform with robust tenancy and private-link networking, using open standards for transparent chargeback. Structure your engagements as a clear value ladder—from a sovereignty scorecard to an architectural review to a paid pilot—to transform your clients’ urgent compliance challenges into your new, high-margin recurring revenue stream.
Your mandate is to make sovereignty an accelerator, not a tax on delivery. Start by picking a pragmatic deployment mode; if constraints put you in a Transitional state, lock down the non-negotiable technical controls like in-region control planes and customer-held keys on day one, with a clear timeline for organizational upgrades. Then, make evidence a native part of your CI/CD pipeline. By treating policy checks like unit tests and publishing immutable audit artifacts with every change, you transform compliance from a manual gate into an automated function that helps your Change Advisory Board and auditors move faster.
Shift your posture from reactive Data Protection Impact Assessment (DPIA) anxiety to being proactively audit-ready. Mandate a baseline of non-negotiable controls in all new procurements, including customer-managed keys (CMK/HSM), metadata residency, and no-egress defaults, and require vendors to provide evidence samples before a deal is signed. This allows you to standardize the provenance of your controls, building a living library of signed policy repositories, software attestations (SBOMs), and retention proofs that gives you a complete, defensible, and time-stamped record of your compliance posture.
Successfully navigating sovereignty requires embracing its complexity. The strategy is inherently multi-dimensional; your legal, organizational, technical, and supply-chain controls must harmonize. A failure in one layer—such as an EU-only operations team undermined by a global control plane—compromises your entire posture.
Furthermore, the landscape is constantly dynamic. Regulations evolve and vendor roadmaps shift, so the winning approach is to choose a deployment mode you can operate today while architecting for portability. This preserves your leverage to pivot as the market changes.
The ultimate advantage comes from making your sovereignty posture measurable. When controls are expressed as code and evidence becomes a real-time API output, the dynamic changes. Audits compress from a weeks-long exercise into a minutes-long verification, freeing your teams to ship innovative products faster and with greater confidence.
Sovereignty isn’t a logo or a location. It’s a stack of enforceable controls and undeniable proofs you can produce on demand. In a landscape being reshaped by stringent EU regulations and unpredictable market shifts, the ability to prove compliance is no longer a theoretical exercise—it is a competitive necessity.
The organizations that win in this new environment will be those that stop treating sovereignty as a tax and reframe it as a source of velocity. They will achieve this by operationalizing a clear framework—like our Four Layers model—and deploying a dedicated sovereignty layer that automates technical enforcement and delivers proof as a service. This is how you build a more resilient, efficient, and defensible business for the future of the European digital economy.